Troubleshooting Active Directory Account Lockouts
A how-to on diagnosing the cause of a (user’s) Active Directory account repeatedly locking out.
Download the Account Lockout Status tools from Microsoft
Below is the Active Directory Solution:
- https://www.microsoft.com/en-us/download/confirmation.aspx?id=15201
- Run the .msi to extract the files then run the LockoutStatus.exe tool (note, run on a domain controller for best performance)
Choose ‘Select Target’ from the File menu
- Enter the user’s account name as the target – if you’re already logged in with a domain Admin account, adding alternate credentials is not necessary.
- The LockoutStatus tool will show the status of the account on the domain DCs including the DCs which registered the account as locked and, crucially, which DCs recorded a bad password (the ‘Bad Pwd Count’ column). The DCs most likely to give the result we need are those reporting one or more bad passwords as listed in the ‘Bad Pwd Count’ column.
Check the Security log on one of these DCs
- Typically, you’ll review the logs of the DC that has the most failed lockouts at that given moment, or the DC that locked first. Make sure to reference the log of the exact minute/second that the lockout occurs based on the output of the LockoutStatus.exe tool.

- In the Security Log of one of the domain controllers which show the account as locked, look for (Event ID 4771 on Server 2008 or Event ID 529 on Server 2003 containing the target username. Specifically, you need the log entries which show Failure code 0x18. Note the client IP Address – This is the address of the machine that reported, or holds, the bad password.
Active Directory: Enable Verbose Logging
- Sometimes, it’s less specific, whereas there is something else logging the event or, it’s hopping through another device but only the last node is logged in the events- You may get a log that looks like this:
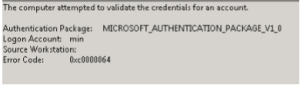
- In this case, we’ll need to enable verbose logging on the DC, and wait for the next failed login attempt by refreshing the status of the LockoutStatus.exe tool. To refresh the status, simply hit F5 in that window.
- To enable Verbose Logging, open an elevated command prompt on the DC that is reporting the lockout and execute the following command: nltest /dbflag:0x2080ffff
- This logs every transaction made to the file: %windir% | debug | netlogon.log (note, you need to run notepad as an administrator to read this file).
- Inside of the netlogon.log file, find the logon attempt made by the user by referencing the exact date/time that LockoutStatus.exe reported and it should list the workstation it came from. Again, be sure to find the record matching the exact minute/second that the lockout of failed attempt occurred in the LockoutStatus.exe tool.
- 11/01 09:11:21 [LOGON] DOMAIN: SamLogon: Transitive Network logon of (null) | UserName from (WorkStationName) Entered
- Once you find that you have located the source of the failed attempts, you will want to shut of verbose logging.
- To do so, enter the following command in the elevated command window: nltest /dbflag:0x0
